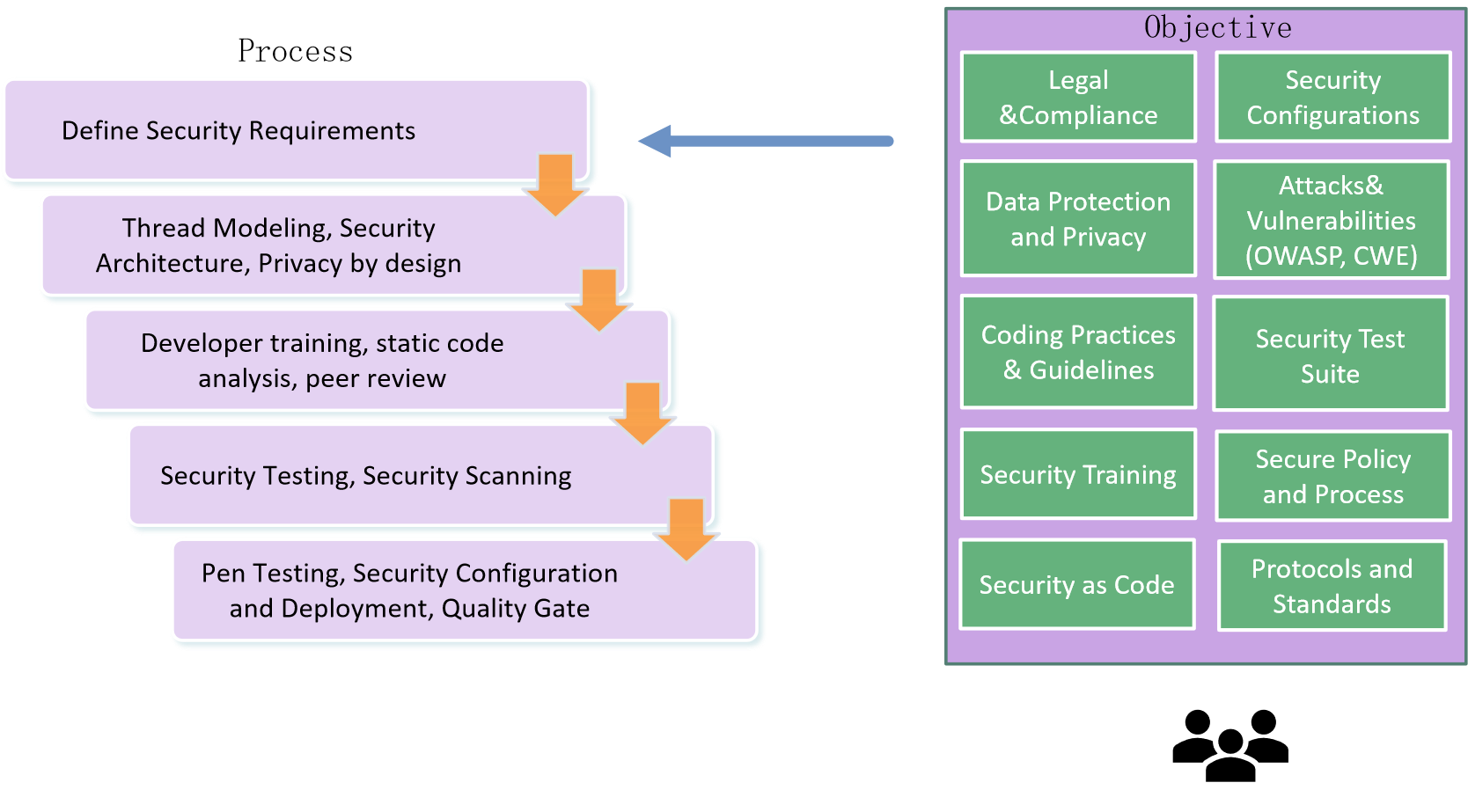
Techtez security framework defines the security objective, process, and tools in every phase of SDLC. This framework is expected to identify and address the security aspects early in the development cycle and ensure a robust and secure application is developed which is free of issues and vulnerabilities.
| SDLC Phase | Process | Tools |
|---|---|---|
| Requirements Elicitation | TEHCTEZ developed a comprehensive questioner to collect the details of security requirements. Collected details like objective, regulatory compliance, web security expectations, IAM, data encryption in transit & rest, encryption standards, enterprise integration, API integration (access & data integrity), software licenses and versions, integrating systems, etc. | Spread sheet based questioner |
| Design | Threat modeling tools are used during the design to identify and mitigate potential security issues early, when they are relatively easy and cost-effective to resolve. | Microsoft Threat modeling |
| Development | Use SAST tools to analyze application source code, byte code and binaries for coding and design conditions that are indicative of security vulnerabilities | SonarLint, FindSecBugs, SpotBugs etc |
| Testing | Dynamic Application Security (DAST) is a black-box security testing methodology in which an application is tested from the outside. The objective of this testing is to identify critical web application vulnerabilities as defined in OWASP (https://owasp.org/). |
Nessus, OpenVAS, ZAP etc. |

This IoT platform designed and implemented using the secure SDLC process as detailed in the previous sections.


TECHTEZ developed / Maintain a telecom application for the US Telecom solution major, this application is used by more than 10 Telcos around the globe.